How to write generic dissectors in Wireshark
Wireshark is a flexible network analyzer, that can also be extended via plugins or dissectors.
A dissector is a kind of plugin that lets Wireshark understand a protocol - in our case, a protocol that is only used by a certain application. There are several reasons to create your own (application-level) protocol over UDP/IP or TCP/IP, such as efficiency (by sending only binary data, formatted in a certain application-specific format).
Wireshark is a very helpful tool during system integration tests, or while developing a networked application. A dissector helps developers and testers check if the applications under test are sending (or receiving) data correctly - if the structure of a certain message is as defined by the protocol, if some fields have invalid values, if an application is sending more (or fewer) messages than expected in a certain timeframe.
WireShark Generic Dissectors - a declarative approach
Wireshark Generic Dissectors (WSGD) is a plugin that lets you define a dissector for your custom protocol, in a declarative manner.
Being declarative is a cool idea - by just saying what the protocol looks like, the content of the dissector is clear to a technical, but non-developer, user. Such protocol descriptions can also be used as documentation, without having to manage different Wireshark API versions (as it may happen with Lua-based dissectors). It's not all fun and games though: this plugin has some (reasonable) limitations, such as not managing text protocols, or requiring an header common to every kind of message described in the protocol.
Let's write a generic dissector
Let's start with the Wireshark Generic Dissector file: it contains some metadata about the protocol. These metadata, consisting of details such as the protocol name, the structure that sketches the header of all messages in the protocol and the main message, are necessary to be efficient when parsing the messages during the capture.
# file custom.wsgd # protocol metadata PROTONAME Custom Protocol over UDP PROTOSHORTNAME Custom PROTOABBREV custom # conditions on which the dissector is applied: # the protocol will be applied on all UDP messages with port = 8756 PARENT_SUBFIELD udp.port PARENT_SUBFIELD_VALUES 8756 # the name of the header structure MSG_HEADER_TYPE T_custom_header # field which permits to identify the message type. MSG_ID_FIELD_NAME msg_id # the main message type - usually it is a fake message, built of one # of the possible messages MSG_MAIN_TYPE T_custom_switch(msg_id) # this token marks the end of the protocol description PROTO_TYPE_DEFINITIONS # refer to the description of the data format include custom.fdesc;
The second file is the data format description: it described the messages of the protocol we're writing a dissector for.
# file custom.fdesc # here, we define an enumerated type to list the type of messages # defined in our protocol enum8 T_custom_msg_type { word_message 0 number_message 1 } # here, we define the structure of the header. # The header (the same for each message type) must... struct T_custom_header { # ... define the order of the data byte_order big_endian; uint32 counter; uint8 size_after_header; # ... contain the field defined as MSG_ID_FIELD_NAME T_custom_msg_type msg_id; } struct T_word_message { T_custom_header header; uint8 word_len; # array of characters char[word_len] word; # "word" messages will always have some unused trailing bytes: # they can be marked as raw(*) - the size is calculated at runtime raw(*) spare; } struct T_number_message { T_custom_header header; uint8 number; bool8 is_even; } # T_custom_switch is the main message (as defined in the protocol description) # according to the parameter msg_id (of type T_custom_msg_type), we define # the main message to be defined by a single message: either T_word_message or T_number_message. switch T_custom_switch T_custom_msg_type { case T_custom_msg_type::word_message: T_word_message ""; case T_custom_msg_type::number_message: T_number_message ""; }
Generating some network traffic...
To verify that the dissector we've written is correct, we are going to build a small client to send some UDP messages to a very simple server.
Let's start with the server: it just receives UDP messages on port 8756, and prints the contents of those messages.
import socketserver class CustomHandler(socketserver.DatagramRequestHandler): def handle(self): data = self.request[0].strip() print(data) if __name__ == "__main__": serv = socketserver.UDPServer(("127.0.0.1", 8756), CustomHandler) serv.serve_forever()
The client sends some data to our server - we just need it to generate some traffic to sniff on Wireshark.
import socket import struct import random import string import time HOST, PORT = "localhost", 8756 # SOCK_DGRAM is the socket type to use for UDP sockets sock = socket.socket(socket.AF_INET, socket.SOCK_DGRAM) # refer to `pydoc struct` HEADER_STRUCT = "".join([ ">", # network byte order "L", # counter "B", # message size "B", # message type (0: word, 1: number) ]) PAYLOAD_WORD_TYPE = HEADER_STRUCT + "".join([ "B", # word length "100s", # string (at most 100 characters) ]) word_struct = struct.Struct(PAYLOAD_WORD_TYPE) PAYLOAD_NUMBER_TYPE = HEADER_STRUCT + "".join([ "B", # number "B", # 0: even, 1: odd ]) number_struct = struct.Struct(PAYLOAD_NUMBER_TYPE) msg_counter = 0 while True: msg_counter += 1 # prepare data to send if random.random() < 0.70: num = random.choice(range(256)) is_even = num & 1 data = number_struct.pack(msg_counter, 2, 1, num, is_even) else: string_len = random.choice(range(100)) the_string = bytes("".join(random.choice(string.ascii_letters+" ") for i in range(string_len)), "ascii") data = word_struct.pack(msg_counter, 101, 0, string_len, the_string) # send the message sock.sendto(data, (HOST, PORT)) # wait 200ms time.sleep(0.2)
Set it up
Wireshark Generic Dissector is a binary plugin, distributed as a .so file - please read the installation procedure. I've summarized what I did to install the plugin and the files we've written so far:
# download the plugin - be sure it's the right one for # the version of Wireshark installed on your system wget http://wsgd.free.fr/300X/generic.so.ubuntu.64.300X.tar.gz # extract the file generic.so unzip ./generic.so.ubuntu.64.300X.tar.gz # install the shared object globally by putting in the right folder sudo cp generic.so /usr/lib/wireshark/plugins/3.0/epan # install the dissector files in the right folder - the same of the shared object sudo cp custom.wsgd /usr/lib/wireshark/plugins/3.0/epan sudo cp custom.fdesc /usr/lib/wireshark/plugins/3.0/epan
Test drive
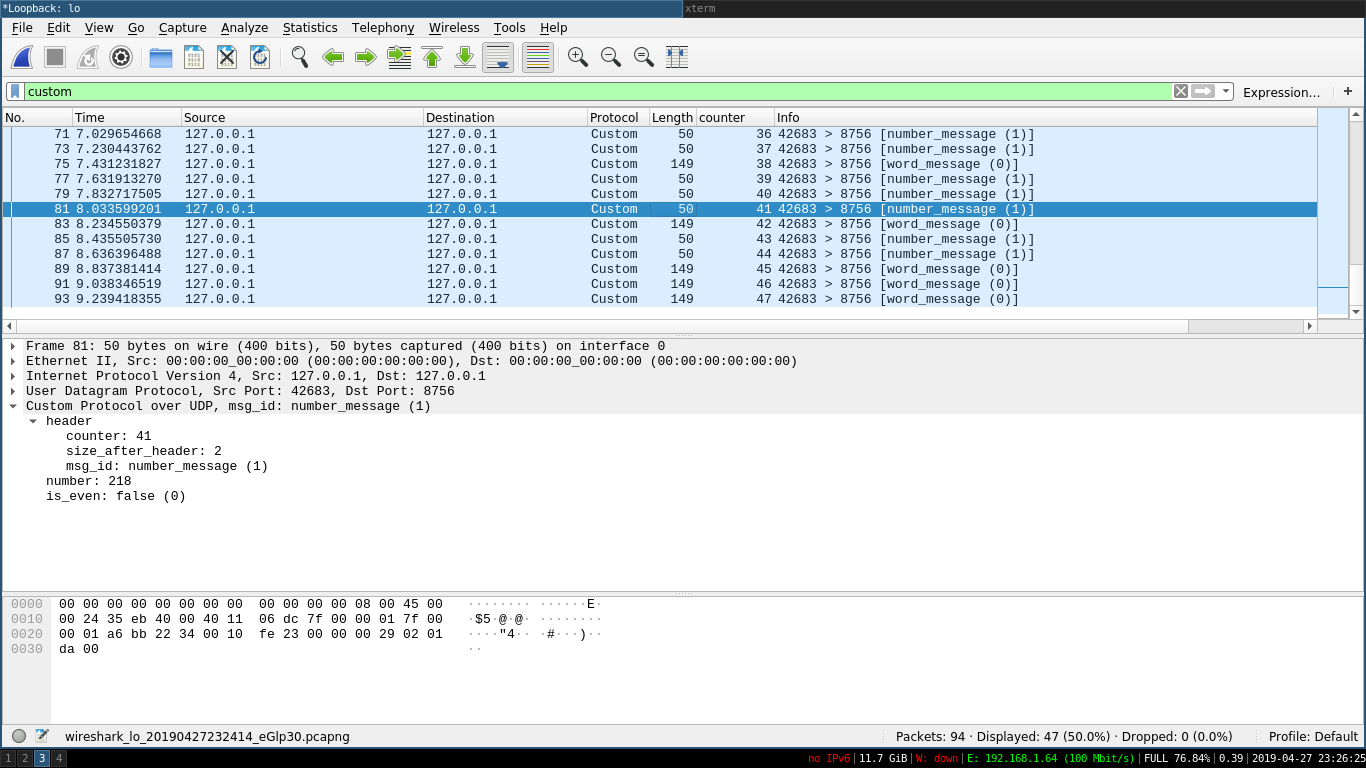
As we can see by the screenshot, we are now able to see the content of the messages our application is sending to the server, without writing a single line of code (other than our application, obviously).
References
- Wireshark Generic Dissector project homepage: http://wsgd.free.fr/index.html
- WSGD file description: http://wsgd.free.fr/wsgd_format.html
- Data format description (fdesc): http://wsgd.free.fr/fdesc_format.html
If you feel that this article helped you, feel free to share it! If you have questions, ask on Twitter, or offer me a coffee to let me keep writing these notes!